compromise assessment malaysia
Performing a compromise assessment gives you confidence in your awareness of. In a letter submitted to its clients on Monday Oct 25 sighted by The Edge CTOS stated that it completed and submitted a compromise assessment to Bank Negara Malaysia BNM last week.
The TIG Compromise Assessment with Infocyte.
. Our Compromise Assessments are an essential business need for all organisations. Comply with industry regulations Avoid straining customer relationships as a results of breaches and leakage of sensitive data. We are focused on identifying the cyber attacks that these first lines of defence may have missed.
The compromised or not state of your environment your ability to identify vulnerabilities your ability to eliminate risks This is essential in running an effective SOC Security Operations Center. The Compromise Assessment is the essential tool to detect the clear and present cyber dangers that already exists in your organization. Contact us for a free quotation today.
It is understood that the assessment was. 46 Appendix 8 Format of Confirmation. Missed our last webinar about Decoding The Latest Guidelines of Compromise Assessment.
Bank Negara Malaysia now encourages financial institutions to conduct a Compromise Assessment CA through a qualified professional service provider. While penetration tests focus on finding vulnerabilities a compromise assessment focuses on whether an organization was breached without knowing it he explains. Compromise Assessment Firmus 2020-06-14T1449110800.
Checkout the virtual tour of EC-Council Cyber Defense The Next Generation SOC state of an art facility in Malaysia with all capabilities to serve clients globally. Increasingly companies around the world understand that Compromise Assessments are a basic business imperative as they enable them to. The virtual tour of EC-Council Cyber Defense The Next Generation Security Operation Center SOC Watch on.
When conducting compromise assessments the priority must not be to reduce false-positives but to reduce false-negatives. Why perform a Compromise Assessment Minimize dwell time Discover if attackers are moving unnoticed in your environment. Malaysia through operations of branches and subsidiaries.
Reduce and control breach impact Receive a comprehensive analysis of your organizations systemic risks and exposures and reduce the risk of attackers stealing financial assets customer data or intellectual property. 2 To identify the presence of any security breaches. Understanding when we are breached and resolving it should be the top priority.
Our solution Using Deloittes Cyber Compromise Assessment CCA on your estate will help identify if there is a current or indicators of a past compromise of your network - utilising the latest threat intelligence and detection techniques. Is Your IT Infrastructure Secured. Usually there are a few reasons companies do a Compromise Assessment.
Risk Management in Technology. Compromise Assessment goes far beyond traditional VAPT. Compromise Assessments independently validate your security posture to discover threats and vulnerabilities your existing defensive tools have missed.
48 Appendix 9 Supervisory Expectations on External Party Assurance. Bank Negara of Malaysias Risk Management in Technology. Upon completion of your assessment.
It takes organizations an average of 191 days to identify a data breach. Compromise Assessments sometimes called Risk Assessments are the first step to a strong cybersecurity strategy. 1 To comply with local laws regulations Eg.
Thats why our methodology involves looking at every possible forensic artefact behaviour and traffic in an environment and conclusively validating its level of risk to business Endpoint Forensic-Depth Analysis. The approach is designed to be light-touch with simple and temporary monitoring installations. Compromise Assessment is the next-generation security assessment service by independent security teams.
Compromise Assessment Malaysia LGMS 1 Cyber Security Provider 7 Who trust LGMS for professional cybersecurity services. In an interview with Information. Our approach to Compromise Assessment The most sophisticated threat actors dedicate their time to finding ways of evading detection from traditional defence mechanisms such as antivirus.
Traditional security testing services like Vulnerability Assessment and Penetration testing focuses only on the application or infrastructure components alone. Now you can watch it here. Appendix 7 Risk Assessment Report.

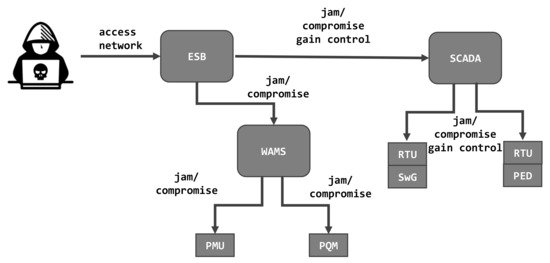
Applied Sciences Free Full Text Threat Modelling And Beyond Novel Approaches To Cyber Secure The Smart Energy System Html
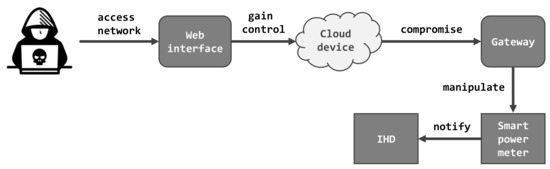
Applied Sciences Free Full Text Threat Modelling And Beyond Novel Approaches To Cyber Secure The Smart Energy System Html
What Is Compromise Assessment The Benefits How It S Different How By Cycraft Technology Corp Cycraft Medium

Cyber Compromise Assessment Deloitte China Risk Advisory

Compromise Assessment Ec Council Global Services Egs

Compromise Assessment 7 Things You Should Know Lgms Blog
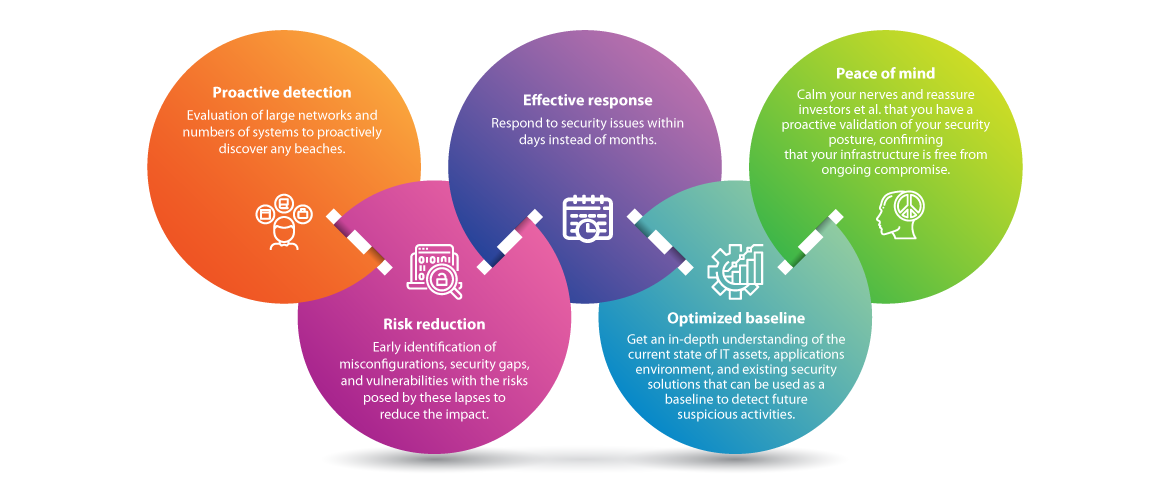
Key Benefits Of Compromise Assessment Infographic Ec Council Global Services Egs

Ioa Vs Ioc Defining Understanding The Differences Crowdstrike

The World Cup Is Here And With It Comes Excitement Pride Competition And Sportsm Physical Education Lessons Education Lesson Plans Physical Education Games
Www Cyberstash Com Wp Content Uploads 2022 04 Asse

Compromise Assessment Condition Zebra Cyber Security Company Malaysia
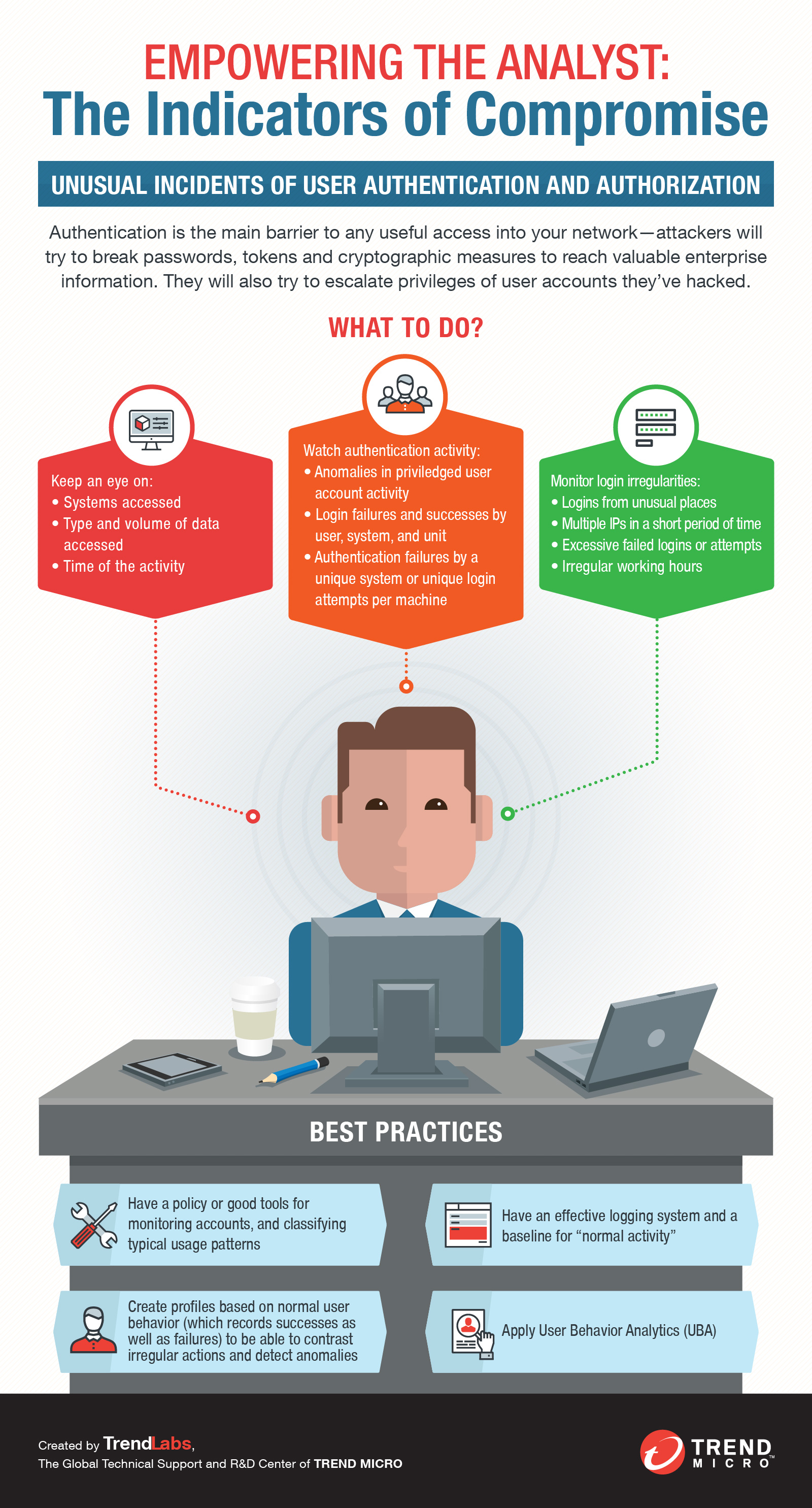
Indicators Of Compromise Definition

Indicators Of Compromise Definition

Compromise Assessment 7 Things You Should Know Lgms Blog

Compromise Assessment Cybereason Assessments

Compromise Assessment Malaysia Uncover Hidden Security Risks Firmus
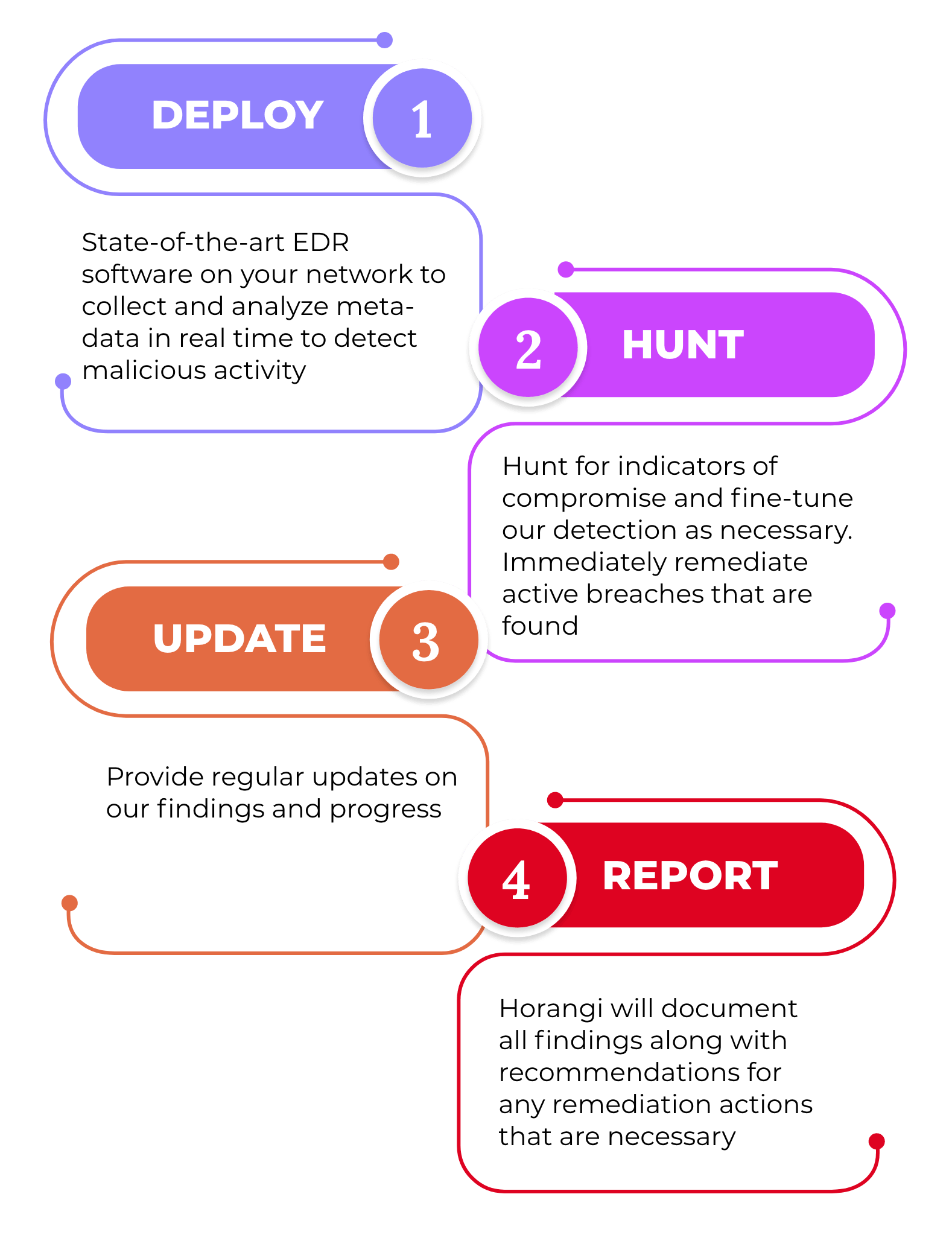



0 Response to "compromise assessment malaysia"
Post a Comment